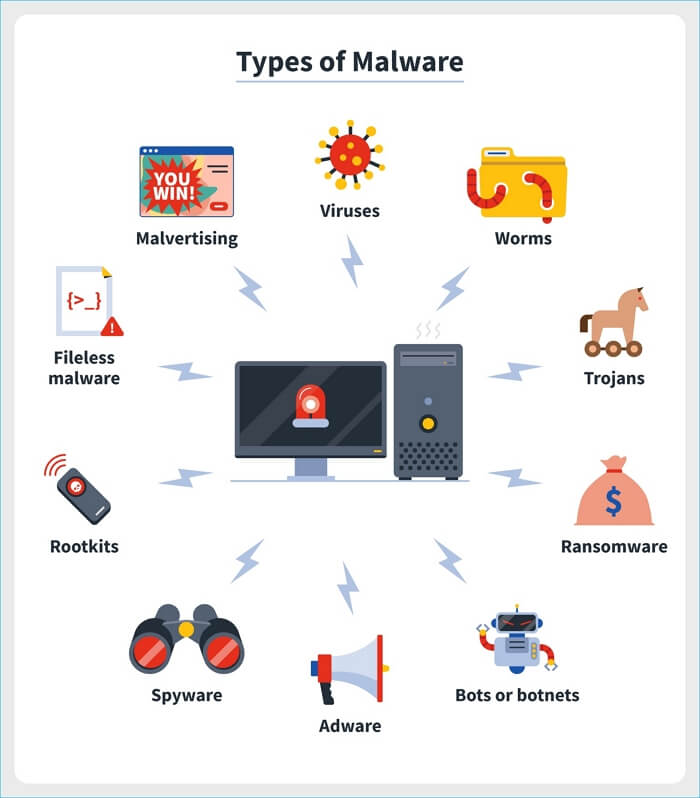
Computer Malware Examples . what does malware look like? hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. learn about different types of malware, how they spread, and how to.
from br.easeus.com
learn about different types of malware, how they spread, and how to. hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. what does malware look like? an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless.
Vírus vs. Ransomware vs. Malware Descubrar as Diferenças em 1 Minuto
Computer Malware Examples hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. what does malware look like? an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. learn about different types of malware, how they spread, and how to. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and.
From study.com
Malware Meaning, Types & Examples Lesson Computer Malware Examples learn about different types of malware, how they spread, and how to. what does malware look like? hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to. Computer Malware Examples.
From dataconomy.com
What Is A Computer Worm Examples And More Dataconomy Computer Malware Examples what does malware look like? hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. an overview of the. Computer Malware Examples.
From www.itbriefcase.net
What Are The Different Types Of Malware? IT Briefcase Computer Malware Examples learn about different types of malware, how they spread, and how to. an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access. Computer Malware Examples.
From www.pandasecurity.com
Types of Malware and How To Prevent Them Panda Security Computer Malware Examples an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. learn about different types of malware, how they spread,. Computer Malware Examples.
From www.eset.com
O que é um malware e como se proteger? Confira! ESET Computer Malware Examples what does malware look like? learn about different types of malware, how they spread, and how to. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. an overview of the most common types of malware, including. Computer Malware Examples.
From www.csoonline.com
Malware explained Definition, examples, detection and recovery CSO Computer Malware Examples learn about different types of malware, how they spread, and how to. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. what does malware look like? an overview of the most common types of malware, including. Computer Malware Examples.
From veritau.co.uk
Ransomware what is it and how can you protect yourself? Veritau Computer Malware Examples malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. what does malware look like? learn about different types of malware, how they spread, and how to. hostile, intrusive, and intentionally nasty, malware seeks to invade, damage,. Computer Malware Examples.
From readibilities.blogspot.com
List Of Computer Viruses Examples Of Computer Virus Computer Malware Examples an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. learn about different types of malware, how they spread,. Computer Malware Examples.
From www.enstep.com
5 Common Computer Viruses that Pose a Threat to Your Data Enstep Computer Malware Examples learn about different types of malware, how they spread, and how to. what does malware look like? hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to. Computer Malware Examples.
From br.easeus.com
Vírus vs. Ransomware vs. Malware Descubrar as Diferenças em 1 Minuto Computer Malware Examples an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. learn about different types of malware, how they spread,. Computer Malware Examples.
From cheapsslsecurity.com
How to Prevent Malware Attacks (7 Ways) Computer Malware Examples an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. what does malware look like? learn about different types of malware, how they spread, and how to. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use. Computer Malware Examples.
From dxoyprhts.blob.core.windows.net
Example Of Computer Virus at Arthur Hitt blog Computer Malware Examples what does malware look like? an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. learn about different types of malware, how they spread, and how to. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use. Computer Malware Examples.
From www.csoonline.com
9 types of malware and how to recognize them CSO Online Computer Malware Examples hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use. Computer Malware Examples.
From cheapsslsecurity.com
Malware vs Virus A 4Minute Explanation of the Differences Computer Malware Examples hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. what does malware look like? malware, short for malicious software, is a blanket term for viruses, worms, trojans and. Computer Malware Examples.
From arstechnica.com
Viruses, Trojans, and worms, oh my The basics on malware Ars Technica Computer Malware Examples an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. learn about different types of malware, how they spread, and how to. hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. what does malware look like? malware,. Computer Malware Examples.
From webapi.bu.edu
😝 Computer virus and types. Computer Virus Types & Examples. 20221021 Computer Malware Examples what does malware look like? an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. learn about different. Computer Malware Examples.
From www.slideshare.net
Computer Viruses Computer Malware Examples an overview of the most common types of malware, including viruses, worms, trojans, ransomware, bots, adware, spyware, rootkits, fileless. what does malware look like? hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. malware, short for malicious software, is a blanket term for viruses, worms, trojans and. Computer Malware Examples.
From vergecampus.com
Computer Viruses, Worms, and Trojans What are They? 2024 Guide Computer Malware Examples hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and. what does malware look like? malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. an overview of the. Computer Malware Examples.